Disabled Accounts
About Disabled Accounts
Qualtrics takes the security and use of its product seriously. The Qualtrics Security team monitors account activity based on a variety of behaviors and metrics. If Qualtrics suspects that harm may be caused to the Cloud Service or its users, for example if an account is flagged as potentially compromised or sending suspicious surveys or emails, then the Security team will review your account and disable it if necessary to prevent malicious activity.
This support page covers the account disabling process, why a Qualtrics account may be disabled, the process to recover an account, how to investigate account abuse, and how an organization can improve their account security.
The Account Disabling Process
When your account is disabled by Qualtrics Security, the following happens:
- The account’s password is reset.
- Any active login sessions are terminated.
- The Qualtrics API token associated with the account is refreshed.
- Attention: Since your API token will be refreshed, any API calls that use this token will no longer work. You will need to update your API calls to use your new token.
Additionally, an email is sent to all Brand Administrators listed for the brand, and the affected user. The email will have the subject line “Qualtrics Security Alert”, and it will include actions taken by Qualtrics Security (listed above), the reason the account was disabled, and the username and user ID of the affected user(s). It also links to this support page for more information.
Why Did Qualtrics Disable My Account?
Qualtrics Security may disable your account to prevent malicious activity and to protect the data in your account. An account may be disabled if Qualtrics Security believes any of the following has occurred (this list is non-exhaustive):
- The account has been compromised (i.e., an unauthorized party has gained access to the account, suspects credentials are compromised).
- The account is in violation of Qualtrics’ Terms of Service or acceptable use policies.
- The account has been used to distribute malware, send phishing emails, or perform other malicious activities.
- Your organization has submitted a request to disable the account.
Recovering Your Account
To recover your Qualtrics account:
- Reset your account password. Resetting your password looks slightly different depending on if your organization uses SSO or not:
- If your organization does not use SSO (i.e., you log in with an email and password), then request a password reset and change your password.
- If your organization does use SSO (i.e., you log in via a third party application, such as Google), then talk to your IT team or Brand Administrator about resetting your SSO password.
- After you’ve recovered your account’s password, contact your Brand Administrator to renable your account.
Qtip: If you don’t know your Brand Administrator’s contact information, reach out to your organization’s IT team.
- You can now log into Qualtrics.
Investigating Abuse
Once the account is recovered and re-enabled, a Brand Administrator will be able to log into the account to investigate login events and activity.
Login Events
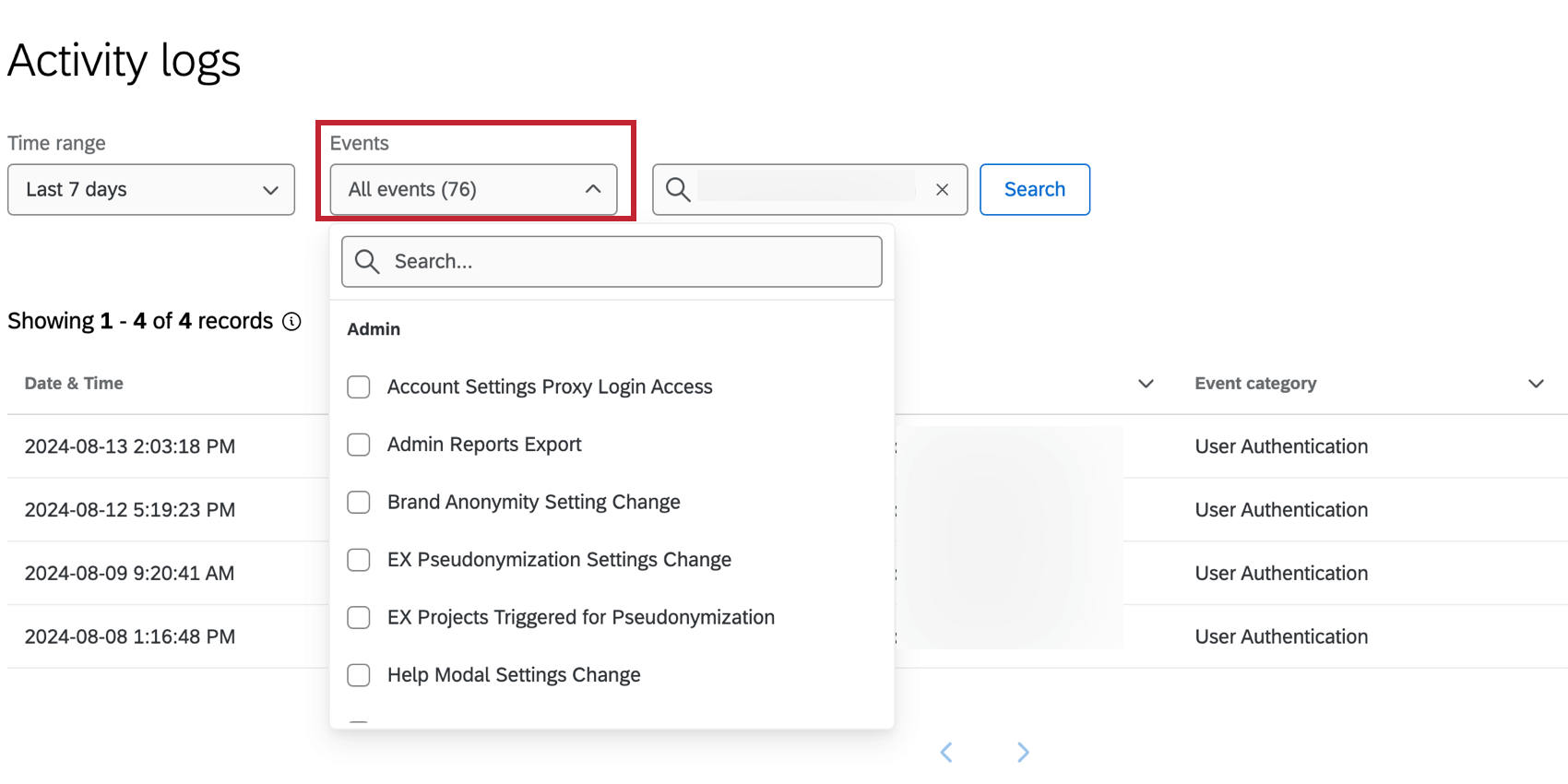
If your Organization has access to the Security Tab, you can look in the Activity Logs and search by Username to find the login event.
- Navigate to Admin.
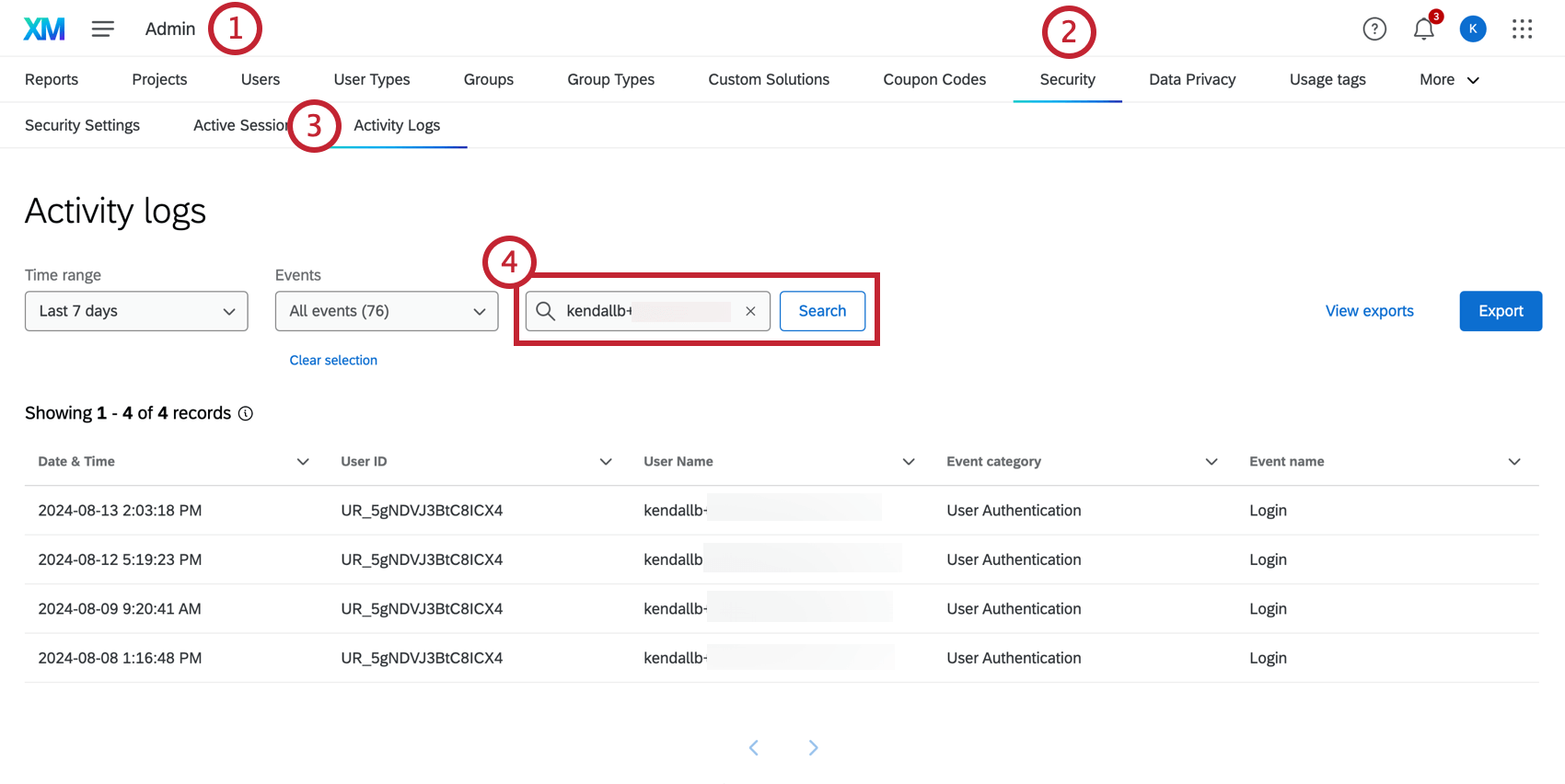
- Select the Security tab.
- Click Activity Logs.
- Enter the username you are investigating into the search box.
If your organization does not have access to the Security Tab, as a Brand Administrator, you can log into the account of the impacted user, and check their Recent Logins.
- Navigate to Admin.
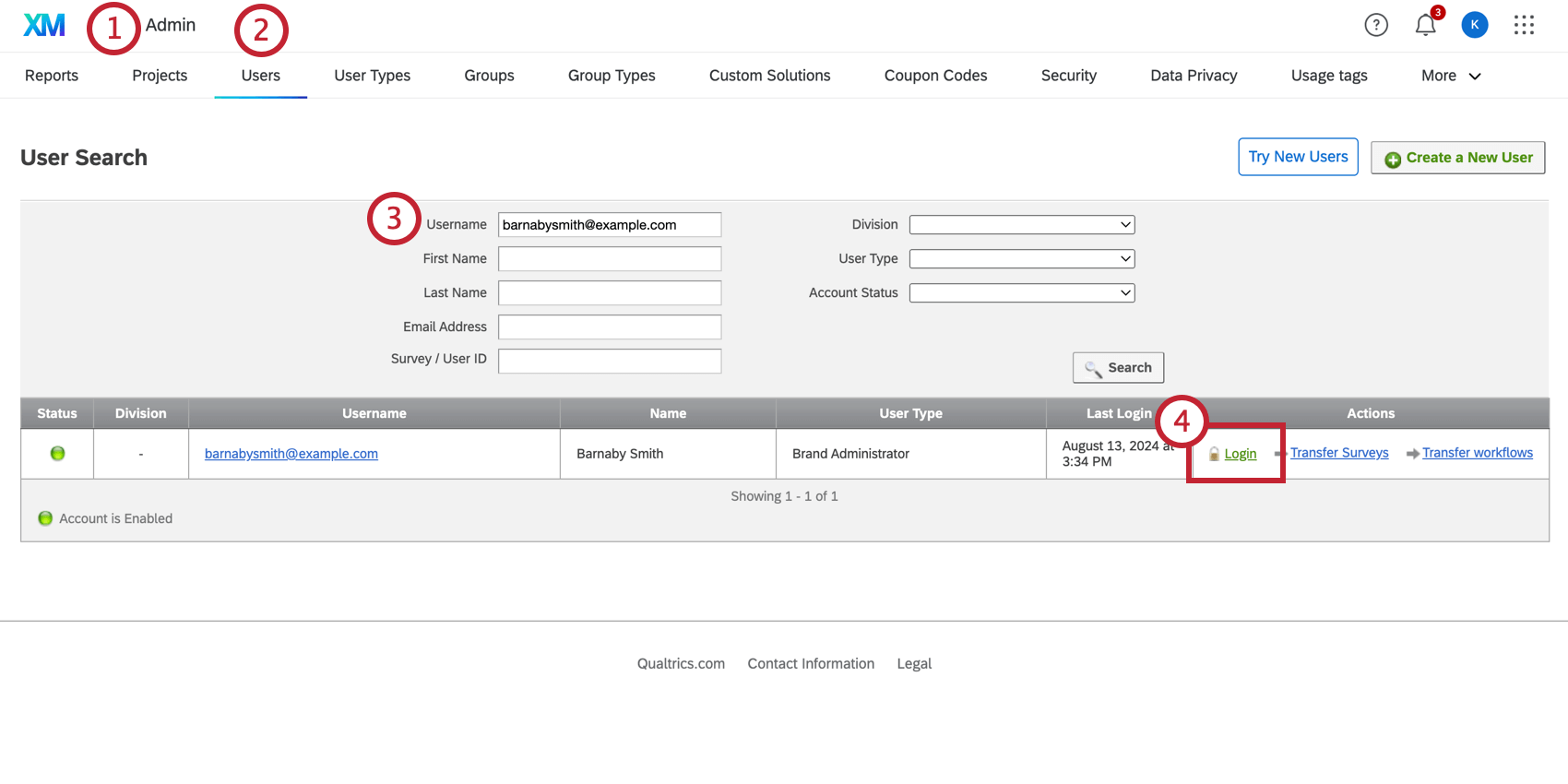
- Select the Users tab.
- Search for the Email Address or User ID of the impacted user.
- Click Login to access their account.
- Navigate to the Account Settings.
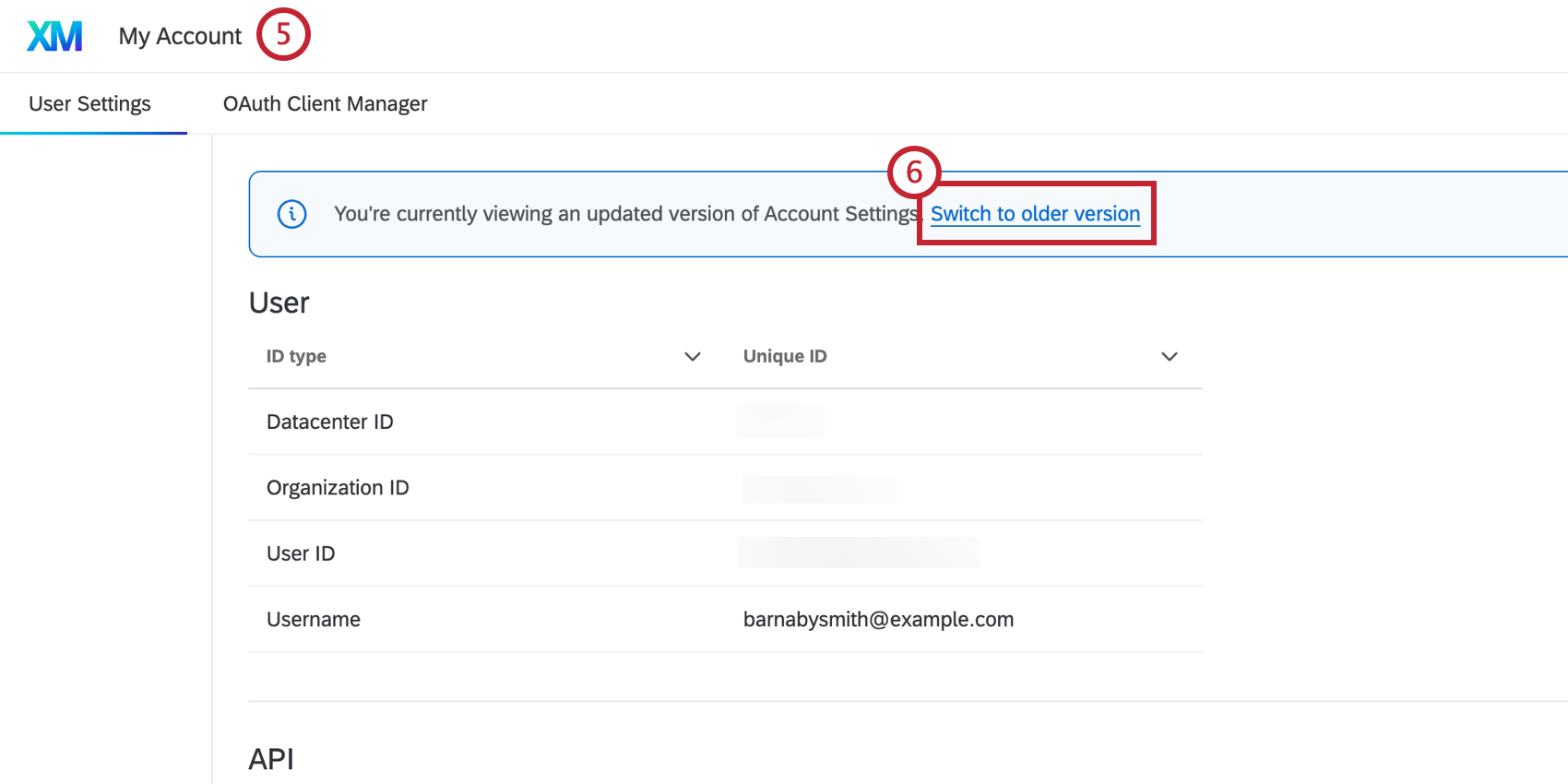
- Click Switch to older version.
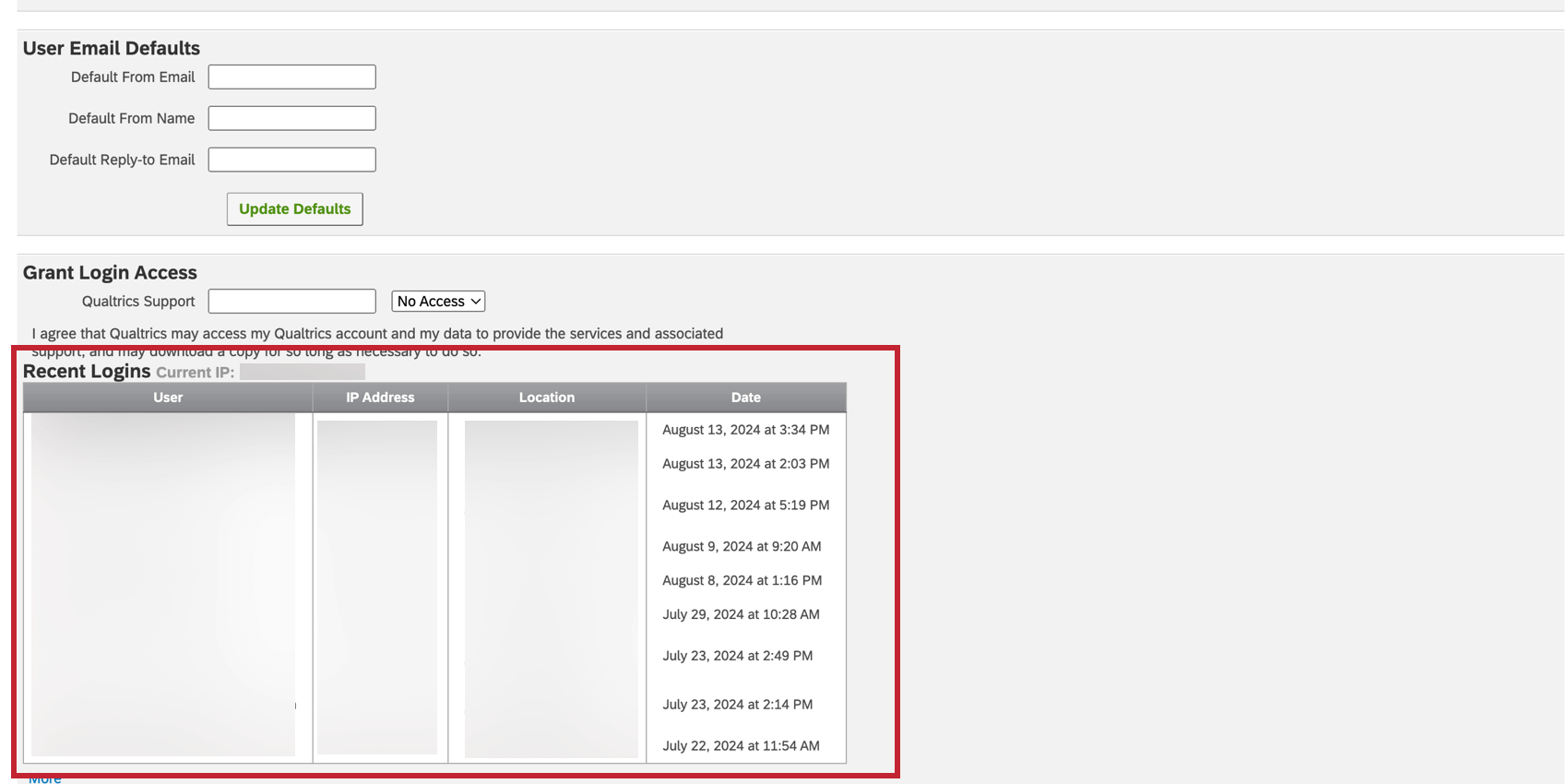
- View the Recent Logins section. Here you can find the IP, location, and date of past logins.
Additional Activity
As a Brand Administrator, once you’ve logged into your user’s account, you can look for other activity that may have taken place. A good place to start would be the Home page, where you can view recently visited surveys. Within those recently visited surveys, you can view Distributions, Data & Analysis, and Contacts / Directories to view activity that may have occurred.
Improving Account Security
While we cannot provide specific details regarding the source of the compromise, common factors include password reuse across multiple platforms, breaches from third-party services, and phishing attempts. We encourage all customers to implement the safeguards listed below to their accounts:
- Create a long and unique password for Qualtrics. You can change your password in user settings, or request a password reset from the login page.
- Brand Administrators should:
- Advise users not to re-use their old password when going through the password reset workflow.
- Strengthen the Password Creation rules for your organization, found in the Organization Settings tab.
- Enable Two Factor Authentication for your organization, found in the Security Tab.
- Enable SSO for your organization if available.
- Disable Qualtrics Login if you enable SSO.
- Ensure that your SSO Configuration is configured in such a way that only legitimate users of your organization can create Qualtrics accounts on your brand. For more information, please see Restricting User Access.
- Restrict access to Qualtrics accounts on your brand to your network’s IP range by enabling the Allowed IP Addresses permission.
- Disable user accounts once they are no longer a member of your organization.